Qemu fsfreeze hook
Tratto da https://kb.kurgan.org/PVE
Uso di Qemu-agent
Abilitando l’agent nella configurazione della VM, e installando l’agent dentro la VM, è possibile gestire alcune funzioni di comunicazione fra host e guest. Una delle funzioni più comode è quella del freeze del file system nel momento in cui viene fatto uno snapshot (per esempio per i backup) per avere dei backup il più possibile congruenti. Per il file system, il semplice fatto di avere l’agente installato e abilitato è sufficiente. Per un database, tuttavia, è opportuno configurare uno script apposta.
Il pacchetto Debian da installare nel guest si chiama qemu-guest-agent
Qemu-agent e Mysql su guest Debian
Per fare interagire Mysql (o Mariadb) con qemu-agent occorre:
- Installare il pacchetto dell’agent
-
Modificare il file di init /etc/init.d/qemu-guest-agent aggiungendo il parametro “-F” nella variabile DAEMON_ARGS, in queso modo: DAEMON_ARGS="-F"
- Riavviare qemu-guest-agent
-
Creare la directory /etc/qemu
-
Creare la directory /etc/qemu/fsfreeze-hook.d
-
Creare lo script /etc/qemu/fsfreeze-hook, contenente quanto segue:
#!/bin/bash # This script is executed when a guest agent receives fsfreeze-freeze and # fsfreeze-thaw command, if it is specified in --fsfreeze-hook (-F) # option of qemu-ga or placed in default path (/etc/qemu/fsfreeze-hook). # When the agent receives fsfreeze-freeze request, this script is issued with # "freeze" argument before the filesystem is frozen. And for fsfreeze-thaw # request, it is issued with "thaw" argument after filesystem is thawed. LOGFILE=/var/log/qga-fsfreeze-hook.log FSFREEZE_D=$(dirname -- "$0")/fsfreeze-hook.d # Check whether file $1 is a backup or rpm-generated file and should be ignored is_ignored_file() { case "$1" in *~ | *.bak | *.orig | *.rpmnew | *.rpmorig | *.rpmsave | *.sample) return 0 ;; esac return 1 } # Iterate executables in directory "fsfreeze-hook.d" with the specified args [ ! -d "$FSFREEZE_D" ] && exit 0 for file in "$FSFREEZE_D"/* ; do is_ignored_file "$file" && continue [ -x "$file" ] || continue printf "$(date): execute $file $@\n" >>$LOGFILE "$file" "$@" >>$LOGFILE 2>&1 STATUS=$? printf "$(date): $file finished with status=$STATUS\n" >>$LOGFILE done exit 0 -
Creare lo script /etc/qemu/fsfreeze-hook.d/mysql-flush.sh contenente quanto segue (nota se occorre o meno inserire il parametro per la password nella variabile MYSQL_OPTS):
#!/bin/bash # Flush MySQL tables to the disk before the filesystem is frozen. # At the same time, this keeps a read lock in order to avoid write accesses # from the other clients until the filesystem is thawed. MYSQL="/usr/bin/mysql" MYSQL_OPTS="-uroot" #"-prootpassword" FIFO=/var/run/mysql-flush.fifo # Check mysql is installed and the server running [ -x "$MYSQL" ] && "$MYSQL" $MYSQL_OPTS < /dev/null || exit 0 flush_and_wait() { printf "FLUSH TABLES WITH READ LOCK \\G\n" trap 'printf "$(date): $0 is killed\n">&2' HUP INT QUIT ALRM TERM read < $FIFO printf "UNLOCK TABLES \\G\n" rm -f $FIFO } case "$1" in freeze) mkfifo $FIFO || exit 1 flush_and_wait | "$MYSQL" $MYSQL_OPTS & # wait until every block is flushed while [ "$(echo 'SHOW STATUS LIKE "Key_blocks_not_flushed"' |\ "$MYSQL" $MYSQL_OPTS | tail -1 | cut -f 2)" -gt 0 ]; do sleep 1 done # for InnoDB, wait until every log is flushed INNODB_STATUS=$(mktemp /tmp/mysql-flush.XXXXXX) [ $? -ne 0 ] && exit 2 trap "rm -f $INNODB_STATUS; exit 1" HUP INT QUIT ALRM TERM while :; do printf "SHOW ENGINE INNODB STATUS \\G" |\ "$MYSQL" $MYSQL_OPTS > $INNODB_STATUS LOG_CURRENT=$(grep 'Log sequence number' $INNODB_STATUS |\ tr -s ' ' | cut -d' ' -f4) LOG_FLUSHED=$(grep 'Log flushed up to' $INNODB_STATUS |\ tr -s ' ' | cut -d' ' -f5) [ "$LOG_CURRENT" = "$LOG_FLUSHED" ] && break sleep 1 done rm -f $INNODB_STATUS ;; thaw) [ ! -p $FIFO ] && exit 1 echo > $FIFO ;; *) exit 1 ;; esac - Rendere eseguibili da root i due script appena creati
Fatto questo, quando si lancia un backup il DB verrà flushato e lockato in scrittura per un secondo circa, il tempo di creare lo snapshot per il backup, poi verrà immediatamente sbloccato. Il risultato, nel log del guest, è una cosa tipo:
Jul 21 14:24:23 web1 qemu-ga: info: guest-fsfreeze called Jul 21 14:24:23 web1 qemu-ga: info: executing fsfreeze hook with arg 'freeze' Jul 21 14:24:23 web1 qemu-ga: info: executing fsfreeze hook with arg 'thaw'
andrea
- Published in Sistemistica, Tips & Tricks, Virtualizzazione
Autenticazione SSSD/LDAP su AD
/etc/portage/package.use
=sys-auth/sssd-1.16.3-r1 ssh sudo >=sys-libs/pam-1.3.0-r2 audit
emerge sssd
/etc/sshd/sssd.conf
[pam] reconnection_retries = 3 [domain/LDAP] id_provider = ldap auth_provider = ldap ldap_schema = AD #ldap_schema = rfc2307bis ldap_access_order = expire ldap_account_expire_policy = ad ldap_force_upper_case_realm = true ldap_id_mapping = true ldap_uri = ldaps://,ldap:// ldap_default_bind_dn = ... ldap_default_authtok = ... ldap_default_authtok_type = password #ldap_referrals = false ldap_search_base = ... #ldap_user_search_base = ... ldap_user_search_base = ... ldap_user_object_class = user ldap_user_principal = userPrincipalName ldap_user_name = sAMAccountName ldap_user_fullname = displayName ldap_group_search_base = ... ldap_group_object_class = group ldap_group_name = sAMAccountName ldap_tls_reqcert = never #ldap_tls_reqcert = hard ldap_tls_cacert = /etc/ssl/certs/ca-certificates.crt ldap_id_use_start_tls = true override_shell = /bin/bash cache_credentials = true enumerate = true #ldap_rfc2307_fallback_to_local_users = true override_homedir = /home/%u #min_id = 10000 #ldap_group_gid = 9999 #override_gid = 9999 #ad_gpo_access_control = disabled access_provider = simple simple_allow_groups = ..., ... #access_provider = ldap #ldap_access_order = filter #ldap_group_member = member #ldap_access_filter = (|(memberOf=CN=...)(memberOf=CN=...))
nsswitch.conf
passwd: compat shadow: compat group: compat passwd: db files nis sss shadow: db files nis sss group: db files nis sss #group: db files nis hosts: files dns networks: files dns services: db files protocols: db files rpc: db files ethers: db files netmasks: files netgroup: files sss bootparams: files sudoers: ldap files sss automount: files aliases: files
/etc/pam.d/system-auth
auth sufficient pam_sss.so forward_pass auth required pam_env.so auth required pam_unix.so try_first_pass likeauth nullok auth optional pam_permit.so account [default=bad success=ok user_unknown=ignore authinfo_unavail=ignore] pam_sss.so account required pam_unix.so account optional pam_permit.so password sufficient pam_sss.so use_authtok password sufficient pam_cracklib.so difok=2 minlen=8 dcredit=2 ocredit=2 retry=3 password required pam_unix.so try_first_pass use_authtok nullok sha512 shadow password optional pam_permit.so session required pam_tty_audit.so enable=* session required pam_mkhomedir.so skel=/etc/skel/ umask=0077 session required pam_limits.so session required pam_env.so session required pam_unix.so session optional pam_permit.so
sshd_config
UsePAM yes
getent passwd
getent groups
andrea
- Published in Sistemistica, Tips & Tricks
HP Tools per il controller SAS [SSACLI]
Crea un file hp.list in /etc/apt/sources.list.d contenente
deb http://downloads.linux.hpe.com/SDR/repo/mcp stretch/current non-free
Importa le chiavi:
curl http://downloads.linux.hpe.com/SDR/hpPublicKey1024.pub | apt-key add - curl http://downloads.linux.hpe.com/SDR/hpPublicKey2048.pub | apt-key add - curl http://downloads.linux.hpe.com/SDR/hpPublicKey2048_key1.pub | apt-key add - curl http://downloads.linux.hpe.com/SDR/hpePublicKey2048_key1.pub | apt-key add -
Aggiorna i repository:
apt-get update apt dist-upgrade
Installa i pacchetti del controller:
apt install ssacli ssaducli amsd hponcfg
Licenze SMARTCACHE
HPE Manual
ssacli ctrl slot=0 lk all show ssacli ctrl slot=0 add lk=3MXBB-P2ZCC-ML82H-PB8CS-ZXXXX
HPE Smart Array P408i-a SR Gen10 in Slot 0 (Embedded)
licensekey 3MXBB-P2ZCC-ML82H-PB8CS-ZLZNR (OK)
Attivare rc.local Rc.local in Debian stretch
Inserire in rc.local:
echo 655360 > /proc/sys/vm/min_free_kbytes
echo 0 > /proc/sys/kernel/hung_task_timeout_secs
echo 1 > /proc/sys/vm/swappiness
echo 50 > /proc/sys/vm/vfs_cache_pressure
echo 1 > /proc/sys/kernel/dmesg_restrict
ssacli controller slot=0 modify cacheratio=70/30
ssacli controller slot=0 modify dwc=enable
HBA=( sda sdb )
for DISK in "${HBA[@]}"
do
echo noop > /sys/block/$DISK/queue/scheduler
echo 1024 > /sys/block/$DISK/queue/nr_requests
echo 1024 > /sys/block/$DISK/queue/read_ahead_kb
sdparm --set WCE=1 /dev/$DISK 2>/dev/null
done
Inserire in .bashrc:
ssacli ctrl all show status ssacli ctrl slot=0 pd all show status ssacli ctrl slot=0 ld all show
In cron.hourly:
#!/bin/bash
# Check for HP Smart Array Controller
ssacli ctrl all show config | grep "Smart Array" &>/dev/null
# If Smart Array Controller exists continue with script if not exit script
if [ $? -eq 0 ]; then
# Check HP Smart Array disk status for string "OK"
ssacli ctrl slot=0 pd all show status | grep physicaldrive | grep -vi "OK" &>/dev/null
# If all disks do not report "OK" then continue with script otherwise exit.
if [ $? -eq 1 ]; then
exit 0
else
# Display hostname, HP serial number, disks and RAID configuration of disks
# that failed
ALERT="ALERT-$(date +%Y%m%d-%H%M%S)"
echo "Hostname: $(hostname)" > /root/$ALERT
echo "HP Serial Number: $(dmidecode -t 1 | grep "Serial" | awk '{print $3}')" >> /root/$ALERT
echo "----------------------------------------------------------------------------" >> /root/$ALERT
ssacli ctrl all show config >> /root/$ALERT
cat /root/$ALERT | mail -s "$(hostname)-$ALERT" <..> -c<..>
ssacli ctrl slot=0 pd all show detail >> /root/$ALERT
exit 1
fi
else
echo "HP Smart Array Card not installed"
exit 0
fi
andrea
- Published in Sistemistica, Tips & Tricks
Reverse Proxy Apache HTTPS High Security and Mod_Security
Listen 443
# security
ServerTokens Prod
ServerSignature Off
# modules
LoadModule allowmethods_module modules/mod_allowmethods.so
<Proxy "balancer://cluster443">
BalancerMember "https://XXX.XXX.XXX.XXX:443" ttl=240 keepalive=On route=1
BalancerMember "https://XXX.XXX.XXX.XXX:443" ttl=240 keepalive=On route=2
ProxySet stickysession=ROUTEID
</Proxy>
<VirtualHost <FQDN>:443>
ServerName <FQDN>
# Status manager bilanciamento
ProxyPass /balancer-manager !
ProxyPass "/" "balancer://cluster443/"
ProxyPassReverse "/" "balancer://cluster443/"
#ProxyPreserveHost On
ProxyRequests On
ProxyVia off
# autenticazione server ------------------------------------------
<IfModule mod_ssl.c>
SSLEngine On
#SSLCipherSuite ALL:!ADH:!EXPORT56:!EXPORT40:!SSLv2:!LOW
SSLCertificateFile <CRT>
SSLCertificateChainFile <PEM>
SSLCertificateKeyFile <KEY>
SSLCACertificateFile <PEM>
SSLProxyEngine On
SSLProxyCheckPeerName off
SSLProxyVerify none
SSLProxyCheckPeerCN off
SSLProxyCheckPeerExpire off
# Cipher Suite e Protocolli
SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLHonorCipherOrder On
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH
</IfModule>
RewriteEngine On
RewriteCond %{SSL:SSL_PROTOCOL} ^SSLv3$
RewriteRule ^.*$ http://<SERVER>/SSLv3/ [L,R=302]
# No HTTP1.0
RewriteCond %{THE_REQUEST} !HTTP/1.1$
RewriteRule .* - [F]
# - direttive generali -------------------------------------------
DocumentRoot <ROOT>
# sicurezza
RequestReadTimeout header=20-40,MinRate=500 body=20-60,MinRate=500
RequestHeader set X-Forwarded-Proto "https" env=HTTPS
Header always set X-XSS-Protection "1; mode=block"
Header always set Content-Security-Policy "upgrade-insecure-requests; default-src https:"
Header always append X-Frame-Options SAMEORIGIN
Header always set X-Content-Type-Options "nosniff"
Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure
FileETag None
TraceEnable off
<Location "/">
AllowMethods GET POST OPTIONS
</Location>
# cache
ExpiresActive On
Header unset Etag
Header unset Cache-Control
Header unset Expires
Header unset Pragma
Header set Cache-Control "private, no-cache, no-store, proxy-revalidate, no-transform"
Header set Pragma "no-cache"
# mod_security
SecRuleEngine DetectionOnly
#SecRule ARGS:testparam "@contains test" "id:1234,deny,status:403,msg:'Our test rule has triggered'"
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_47_common_exceptions.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_20_protocol_violations.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_23_request_limits.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_42_tight_security.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_21_protocol_anomalies.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_41_xss_attacks.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_50_outbound.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_45_trojans.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_60_correlation.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_59_outbound_blocking.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_40_generic_attacks.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_49_inbound_blocking.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_41_sql_injection_attacks.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_30_http_policy.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_35_bad_robots.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_48_local_exceptions.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_55_marketing.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_47_skip_outbound_checks.conf
#IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_42_comment_spam.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_13_xml_enabler.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_11_avs_traffic.conf
#IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_25_cc_known.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_16_session_hijacking.conf
#IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_55_application_defects.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_49_header_tagging.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_46_av_scanning.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_16_username_tracking.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_43_csrf_protection.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_16_authentication_tracking.conf
#IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_10_ignore_static.conf
IncludeOptional /etc/modsecurity/git/crs-setup.conf
IncludeOptional /etc/modsecurity/git/REQUEST-901-INITIALIZATION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9001-DRUPAL-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9003-NEXTCLOUD-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9004-DOKUWIKI-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9005-CPANEL-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-905-COMMON-EXCEPTIONS.conf
IncludeOptional /etc/modsecurity/git/REQUEST-910-IP-REPUTATION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-911-METHOD-ENFORCEMENT.conf
IncludeOptional /etc/modsecurity/git/REQUEST-912-DOS-PROTECTION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-913-SCANNER-DETECTION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-914-FILE-DETECTION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-920-PROTOCOL-ENFORCEMENT.conf
IncludeOptional /etc/modsecurity/git/REQUEST-921-PROTOCOL-ATTACK.conf
IncludeOptional /etc/modsecurity/git/REQUEST-930-APPLICATION-ATTACK-LFI.conf
IncludeOptional /etc/modsecurity/git/REQUEST-931-APPLICATION-ATTACK-RFI.conf
IncludeOptional /etc/modsecurity/git/REQUEST-932-APPLICATION-ATTACK-RCE.conf
IncludeOptional /etc/modsecurity/git/REQUEST-933-APPLICATION-ATTACK-PHP.conf
IncludeOptional /etc/modsecurity/git/REQUEST-941-APPLICATION-ATTACK-XSS.conf
IncludeOptional /etc/modsecurity/git/REQUEST-942-APPLICATION-ATTACK-SQLI.conf
IncludeOptional /etc/modsecurity/git/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-944-APPLICATION-ATTACK-JAVA.conf
IncludeOptional /etc/modsecurity/git/REQUEST-949-BLOCKING-EVALUATION.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-950-DATA-LEAKAGES.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-951-DATA-LEAKAGES-SQL.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-952-DATA-LEAKAGES-JAVA.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-953-DATA-LEAKAGES-PHP.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-954-DATA-LEAKAGES-IIS.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-959-BLOCKING-EVALUATION.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-980-CORRELATION.conf
SecAuditEngine On
# SecAuditEngine RelevantOnly
# SecAuditLogRelevantStatus ^1-5
# SecAuditLogParts ABCIFHZ
SecAuditLogType Serial
SecAuditLog /var/log/apache2/modsec_audit.log
</VirtualHost>
andrea
- Published in Networking, Sistemistica, Tips & Tricks
Debian Bonding LACP con Switch HP 1820-24G
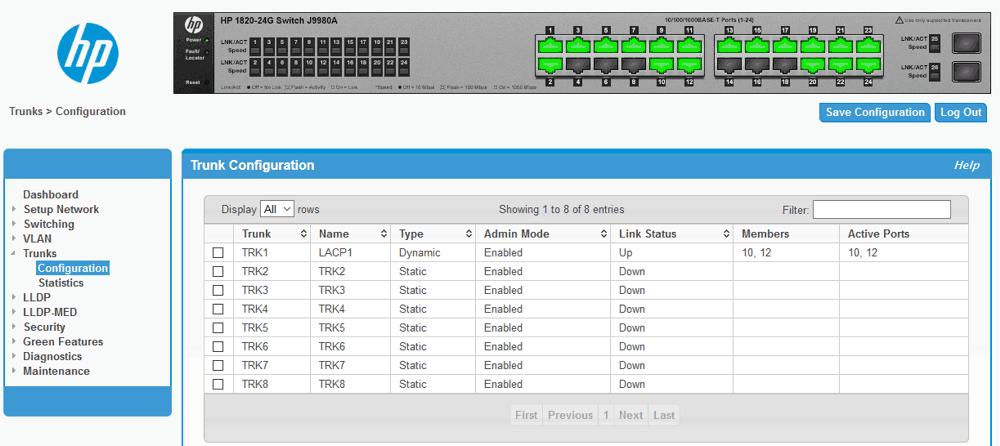
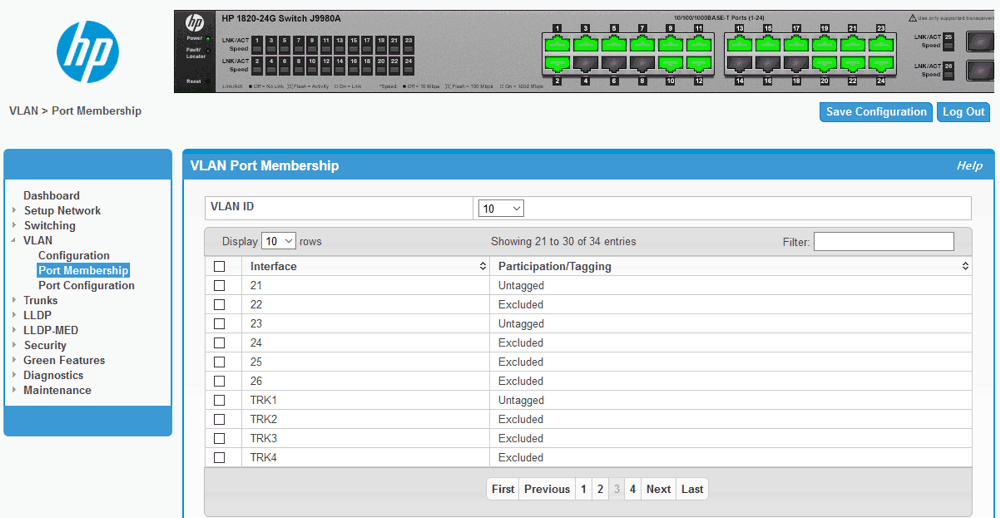
Una volta configurato lo switch HP 1820-24G Switch J9980A per avere il port trunking tra le porte selezionate ed eventualmente aver assegnato il trunk alla VLAN si passa alla configurazione del sistema.
Attenzione che HP chiama Trunk dinamico la modalità LACP.
Ho trovato in alcuni howto questa specifica.
Male non dovrebbe fare.
echo "mii" >> /etc/modules
Si passa alla configurazione dell file /etc/network/interfaces in questo modo.
auto lo
iface lo inet loopback
iface enp2s0f0 inet manual
post-up ifconfig enp2s0f0 txqueuelen 5000 && ifconfig enp2s0f0 mtu 9000
iface enp2s0f1 inet manual
post-up ifconfig enp2s0f1 txqueuelen 5000 && ifconfig enp2s0f1 mtu 9000
auto bond0
iface bond0 inet manual
bond-slaves enp2s0f0 enp2s0f1
bond-mode 802.3ad
bond-miimon 100
bond-downdelay 200
bond-updelay 200
bond-lacp-rate 1
bond-xmit-hash-policy layer2+3
post-up ifconfig bond0 mtu 9000 && ifconfig bond0 txqueuelen 5000
auto vmbr0
iface vmbr0 inet static
address 172.16.5.10
netmask 255.255.255.0
bridge_ports bond0
bridge_stp off
bridge_fd 0
post-up ifconfig vmbr0 mtu 9000 && ifconfig vmbr0 txqueuelen 5000
A questo punto dopo il riavvio il Bond/Trunk risulterà attivo.
# dmesg
igb 0000:02:00.0 enp2s0f0: igb: enp2s0f0 NIC Link is Up 1000 Mbps Full Duplex, Flow Control: None bond0: link status up for interface enp2s0f0, enabling it in 0 ms bond0: link status definitely up for interface enp2s0f0, 1000 Mbps full duplex bond0: Warning: No 802.3ad response from the link partner for any adapters in the bond bond0: first active interface up! vmbr0: port 1(bond0) entered blocking state vmbr0: port 1(bond0) entered forwarding state IPv6: ADDRCONF(NETDEV_CHANGE): vmbr0: link becomes ready igb 0000:02:00.1 enp2s0f1: igb: enp2s0f1 NIC Link is Up 1000 Mbps Full Duplex, Flow Control: None bond0: link status up for interface enp2s0f1, enabling it in 200 ms bond0: link status definitely up for interface enp2s0f1, 1000 Mbps full duplex
# cat /proc/net/bonding/bond0
Ethernet Channel Bonding Driver: v3.7.1 (April 27, 2011)
Bonding Mode: IEEE 802.3ad Dynamic link aggregation
Transmit Hash Policy: layer2+3 (2)
MII Status: up
MII Polling Interval (ms): 100
Up Delay (ms): 200
Down Delay (ms): 200
802.3ad info
LACP rate: fast
Min links: 0
Aggregator selection policy (ad_select): stable
System priority: 65535
System MAC address: 90:e2:ba:74:28:f8
Active Aggregator Info:
Aggregator ID: 1
Number of ports: 2
Actor Key: 9
Partner Key: 54
Partner Mac Address: 70:10:6f:71:3a:80
Slave Interface: enp2s0f0
MII Status: up
Speed: 1000 Mbps
Duplex: full
Link Failure Count: 0
Permanent HW addr: 90:e2:ba:74:28:f8
Slave queue ID: 0
Aggregator ID: 1
Actor Churn State: none
Partner Churn State: none
Actor Churned Count: 0
Partner Churned Count: 0
details actor lacp pdu:
system priority: 65535
system mac address: 90:e2:ba:74:28:f8
port key: 9
port priority: 255
port number: 1
port state: 63
details partner lacp pdu:
system priority: 32768
system mac address: 70:10:6f:71:3a:80
oper key: 54
port priority: 128
port number: 12
port state: 61
Slave Interface: enp2s0f1
MII Status: up
Speed: 1000 Mbps
Duplex: full
Link Failure Count: 0
Permanent HW addr: 90:e2:ba:74:28:f9
Slave queue ID: 0
Aggregator ID: 1
Actor Churn State: none
Partner Churn State: none
Actor Churned Count: 0
Partner Churned Count: 0
details actor lacp pdu:
system priority: 65535
system mac address: 90:e2:ba:74:28:f8
port key: 9
port priority: 255
port number: 2
port state: 63
details partner lacp pdu:
system priority: 32768
system mac address: 70:10:6f:71:3a:80
oper key: 54
port priority: 128
port number: 10
port state: 61
andrea
- Published in Networking, Sistemistica, Tips & Tricks
Centos 7 Cluster PCS
Installo due VM in VirtualBox identiche (4C, 4Gb RAM, 32Gb HDD) con una versione minimale di Centos 7 aggiornata.
Aggiorno il kernel a 4.16 dal repository elrepo.
# rpm --import https://www.elrepo.org/RPM-GPG-KEY-elrepo.org # rpm -Uvh http://www.elrepo.org/elrepo-release-7.0-3.el7.elrepo.noarch.rpm # yum --disablerepo="*" --enablerepo="elrepo-kernel" list available # yum --enablerepo=elrepo-kernel install kernel-ml kernel-ml-devel
Edito il file /etc/default/grub
GRUB_TIMEOUT=5 GRUB_DEFAULT=0 GRUB_DISABLE_SUBMENU=true GRUB_TERMINAL_OUTPUT="console" GRUB_CMDLINE_LINUX="rd.lvm.lv=centos/root rd.lvm.lv=centos/swap crashkernel=auto rhgb quiet" GRUB_DISABLE_RECOVERY="true"
Ed eseguo per attivare la modifica precedente.
# grub2-mkconfig -o /boot/grub2/grub.cfg
Aggiungo qualche pacchetto.
# yum install epel-release.noarch # yum update # yum group install "Development Tools" # yum install bzip2 net-tools psmisc nmap acpid unzip
Modifico /etc/hosts sui due nodi.
192.168.254.83 nodeA.netlite.it nodeA 192.168.254.84 nodeB.netlite.it nodeB
Installo i numerosi pacchetti necessari al cluster.
# yum install pcs fence-agents-all -y
Aggiungo le regole di firewalling.
# firewall-cmd --permanent --add-service=high-availability # firewall-cmd --add-service=high-availability # firewall-cmd --list-service dhcpv6-client ssh high-availability
Modifico la password dell’utente hacluster.
# passwd hacluster Changing password for user hacluster. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully.
Avvio i servizi.
# systemctl start pcsd.service # systemctl enable pcsd.service
Autorizzo i nodi del cluster.
# pcs cluster auth nodeA.netlite.it nodeB.netlite.it Username: hacluster Password: nodeA.netlite.it: Authorized nodeB.netlite.it: Authorized
Inizializzo il cluster.
# pcs cluster setup --start --name ClusterTest nodeA.netlite.it nodeB.netlite.it Destroying cluster on nodes: nodeA.netlite.it, nodeB.netlite.it... nodeA.netlite.it: Stopping Cluster (pacemaker)... nodeB.netlite.it: Stopping Cluster (pacemaker)... nodeB.netlite.it: Successfully destroyed cluster nodeA.netlite.it: Successfully destroyed cluster Sending 'pacemaker_remote authkey' to 'nodeA.netlite.it', 'nodeB.netlite.it' nodeA.netlite.it: successful distribution of the file 'pacemaker_remote authkey' nodeB.netlite.it: successful distribution of the file 'pacemaker_remote authkey' Sending cluster config files to the nodes... nodeA.netlite.it: Succeeded nodeB.netlite.it: Succeeded Starting cluster on nodes: nodeA.netlite.it, nodeB.netlite.it... nodeB.netlite.it: Starting Cluster... nodeA.netlite.it: Starting Cluster... Synchronizing pcsd certificates on nodes nodeA.netlite.it, nodeB.netlite.it... nodeA.netlite.it: Success nodeB.netlite.it: Success Restarting pcsd on the nodes in order to reload the certificates... nodeA.netlite.it: Success nodeB.netlite.it: Success
Abilito il cluster.
# pcs cluster enable --all
Visualizzo lo stato.
# pcs cluster status Cluster Status: Stack: corosync Current DC: nodeA.netlite.it (version 1.1.16-12.el7_4.8-94ff4df) - partition with quorum Last updated: Tue Apr 3 13:02:21 2018 Last change: Tue Apr 3 13:00:43 2018 by hacluster via crmd on nodeA.netlite.it 2 nodes configured 0 resources configured PCSD Status: nodeA.netlite.it: Online nodeB.netlite.it: Online
Status dettagliati.
# pcs status Cluster name: ClusterTest WARNING: no stonith devices and stonith-enabled is not false Stack: corosync Current DC: nodeA.netlite.it (version 1.1.16-12.el7_4.8-94ff4df) - partition with quorum Last updated: Tue Apr 3 13:02:53 2018 Last change: Tue Apr 3 13:00:43 2018 by hacluster via crmd on nodeA.netlite.it 2 nodes configured 0 resources configured Online: [ nodeA.netlite.it nodeB.netlite.it ] No resources Daemon Status: corosync: active/enabled pacemaker: active/enabled pcsd: active/enabled
Disabilito i device stonith (meglio non farlo ma per test è ok).
# pcs property set stonith-enabled=falseIn caso sia necessario attivare i devices qui c’è un buon punto di partenza STONITH.
Configuro un FS.
# pcs resource create httpd_fs Filesystem device="/dev/mapper/vg_apache-lv_apache" directory="/var/www" fstype="ext4" --group apache
Configuro un VIP.
# pcs resource create httpd_vip IPaddr2 ip=192.168.12.100 cidr_netmask=24 --group apache
Configuro un servizio.
# firewall-cmd --add-service=http # firewall-cmd --permanent --add-service=http # pcs resource create httpd_ser apache configfile="/etc/httpd/conf/httpd.conf" statusurl="http://127.0.0.1/server-status" --group apache
Disabilita un nodo.
# pcs cluster stop nodeA.netlite.it
Comandi utili.
# pcs resource move apache nodeA.netlite.it # pcs resource stop apache nodeB.netlite.it # pcs resource disable apache nodeB.netlite.it # pcs resource enable apache nodeB.netlite.it # pcs resource restart apache
andrea
- Published in Non categorizzato, Sistemistica, Tips & Tricks, Virtualizzazione
centos 7 cluster
Procedura di setup Centos 7:
yum install epel-release.noarch yum install net-tools yum install psmisc yum install httpd yum install perl yum install perl-Digest-MD5 rpm --import https://www.elrepo.org/RPM-GPG-KEY-elrepo.org rpm -Uvh http://www.elrepo.org/elrepo-release-7.0-2.el7.elrepo.noarch.rpm yum install -y kmod-drbd84 drbd84-utils crm_verify -L -V /bin/systemctl start pacemaker.service crmadmin configure property stonith-enabled=false service corosync restart service pacemaker restart yum install nmap yum install open-vm-tools service vmtoolsd start systemctl enable vmtoolsd yum install acpid yum install unzip yum install mod_ssl.x86_64
Configurazione cluster unicast:
logging {
fileline: off
to_logfile: yes
logfile: /var/log/cluster/corosync.log
to_stderr: no
debug: off
timestamp: on
to_syslog: yes
logger_subsys {
subsys: QUORUM
debug: off
}
}
totem {
version: 2
token: 3000
secauth: on
rrp_mode: active
interface {
member {
memberaddr: 172.31.252.41
}
member {
memberaddr: 172.31.252.42
}
ringnumber: 0
bindnetaddr: 172.31.252.0
mcastport: 694
ttl: 1
}
transport: udpu
}
quorum {
provider: corosync_votequorum
expected_votes: 2
}
</code>
Configurazione Apache come reverse proxy:
<code>
<VirtualHost *:80>
ServerName webmail.xxxx.it
Redirect / https://webmail.xxxx.it/
# ProxyRequests Off
# <Proxy *>
# Order deny,allow
# Allow from all
# </Proxy>
# ProxyPass / http://XX.XX.XX.XX/
# ProxyPassReverse / http://XX.XX.XX.XX/
</VirtualHost>
<VirtualHost *:443>
ServerName webmail.xxxx.it
RewriteEngine on
ProxyPass / http://XX.XX.XX.XX/ retry=0 ttl=120 timeout=120
ProxyPassReverse / http://XX.XX.XX.XX/
<IfModule mod_ssl.c>
SSLEngine On
SSLProtocol all -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS !RC4"
#SSLSessionCache shmcb:/run/httpd/sslcache(512000)
#SSLSessionCacheTimeout 300
#128bit
#SSLProtocol ALL -SSLv2
#SSLCipherSuite ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AESGCM:RSA+AES:RSA+3DES:!aNULL:!MD5:!DS
# 40 bit
#SSLCipherSuite ALL:!ADH:!EXPORT56:!EXPORT40:!SSLv2:!LOW
SSLCertificateFile /etc/httpd/ssl/2017/STAR_xxxx_it.crt
SSLCertificateChainFile /etc/httpd/ssl/2017/COMODORSADomainValidationSecureServerCA.crt
SSLCertificateKeyFile /etc/httpd/ssl/2017/xxxx.it.key
ErrorDocument 403 http://www.xxxx.it/
ErrorDocument 404 http://www.xxxx.it/
</IfModule>
ProxyRequests on
ProxyVia on
AddOutputFilterByType SUBSTITUTE text/html
</VirtualHost>
Configurazione di sicurezza vari servizi:
https://cipherli.st/
- Published in Cluster, Sistemistica, Tips & Tricks
Corosync/Pacemaker in Centos 7 con LCMC
Corosync/Pacemaker in Centos 7 con LCMC
Pacchetti da installare
yum install perl yum install perl-Digest-MD5 yum install epel-release rpm -ivh http://www.elrepo.org/elrepo-release-7.0-2.el7.elrepo.noarch.rpm rpm --import /etc/pki/rpm-gpg/RPM-GPG-KEY-elrepo.org yum update yum install kmod-drbd90 drbd90-utils yum install acpid yum install open-vm-tools
/etc/corosync/corosync.conf
logging {
fileline: off
to_logfile: yes
logfile: /var/log/cluster/corosync.log
to_stderr: no
debug: off
timestamp: on
to_syslog: yes
logger_subsys {
subsys: QUORUM
debug: off
}
}
totem {
version: 2
token: 3000
secauth: on
rrp_mode: active
transport: udpu
}
nodelist {
node {
ring0_addr: 172.21.8.131
nodeid: 1
}
node {
ring0_addr: 172.21.8.132
nodeid: 2
}
}
quorum {
provider: corosync_votequorum
two_node: 1
expected_votes: 2
}
systemctl enable corosync
systemctl enable pacemaker
reboot
andrea
- Published in Sistemistica, Tips & Tricks, vpn
tema vim
.vimrc
#execute pathogen#infect() syntax on filetype plugin indent on set nowrap set t_Co=256 set background=dark colorscheme PaperColor
Tema PaperColor
PaperColor-Dark
Wget in /.vim/colors/
wget https://raw.githubusercontent.com/NLKNguyen/papercolor-theme/master/colors/PaperColor.vim
andrea
- Published in Sistemistica, Tips & Tricks, vpn