Reverse Proxy Apache HTTPS High Security and Mod_Security
Listen 443
# security
ServerTokens Prod
ServerSignature Off
# modules
LoadModule allowmethods_module modules/mod_allowmethods.so
<Proxy "balancer://cluster443">
BalancerMember "https://XXX.XXX.XXX.XXX:443" ttl=240 keepalive=On route=1
BalancerMember "https://XXX.XXX.XXX.XXX:443" ttl=240 keepalive=On route=2
ProxySet stickysession=ROUTEID
</Proxy>
<VirtualHost <FQDN>:443>
ServerName <FQDN>
# Status manager bilanciamento
ProxyPass /balancer-manager !
ProxyPass "/" "balancer://cluster443/"
ProxyPassReverse "/" "balancer://cluster443/"
#ProxyPreserveHost On
ProxyRequests On
ProxyVia off
# autenticazione server ------------------------------------------
<IfModule mod_ssl.c>
SSLEngine On
#SSLCipherSuite ALL:!ADH:!EXPORT56:!EXPORT40:!SSLv2:!LOW
SSLCertificateFile <CRT>
SSLCertificateChainFile <PEM>
SSLCertificateKeyFile <KEY>
SSLCACertificateFile <PEM>
SSLProxyEngine On
SSLProxyCheckPeerName off
SSLProxyVerify none
SSLProxyCheckPeerCN off
SSLProxyCheckPeerExpire off
# Cipher Suite e Protocolli
SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLHonorCipherOrder On
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH
</IfModule>
RewriteEngine On
RewriteCond %{SSL:SSL_PROTOCOL} ^SSLv3$
RewriteRule ^.*$ http://<SERVER>/SSLv3/ [L,R=302]
# No HTTP1.0
RewriteCond %{THE_REQUEST} !HTTP/1.1$
RewriteRule .* - [F]
# - direttive generali -------------------------------------------
DocumentRoot <ROOT>
# sicurezza
RequestReadTimeout header=20-40,MinRate=500 body=20-60,MinRate=500
RequestHeader set X-Forwarded-Proto "https" env=HTTPS
Header always set X-XSS-Protection "1; mode=block"
Header always set Content-Security-Policy "upgrade-insecure-requests; default-src https:"
Header always append X-Frame-Options SAMEORIGIN
Header always set X-Content-Type-Options "nosniff"
Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure
FileETag None
TraceEnable off
<Location "/">
AllowMethods GET POST OPTIONS
</Location>
# cache
ExpiresActive On
Header unset Etag
Header unset Cache-Control
Header unset Expires
Header unset Pragma
Header set Cache-Control "private, no-cache, no-store, proxy-revalidate, no-transform"
Header set Pragma "no-cache"
# mod_security
SecRuleEngine DetectionOnly
#SecRule ARGS:testparam "@contains test" "id:1234,deny,status:403,msg:'Our test rule has triggered'"
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_47_common_exceptions.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_20_protocol_violations.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_23_request_limits.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_42_tight_security.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_21_protocol_anomalies.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_41_xss_attacks.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_50_outbound.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_45_trojans.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_60_correlation.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_59_outbound_blocking.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_40_generic_attacks.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_49_inbound_blocking.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_41_sql_injection_attacks.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_30_http_policy.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_35_bad_robots.conf
IncludeOptional /etc/modsecurity/base_rules/modsecurity_crs_48_local_exceptions.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_55_marketing.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_47_skip_outbound_checks.conf
#IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_42_comment_spam.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_13_xml_enabler.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_11_avs_traffic.conf
#IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_25_cc_known.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_16_session_hijacking.conf
#IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_55_application_defects.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_49_header_tagging.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_46_av_scanning.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_16_username_tracking.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_43_csrf_protection.conf
IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_16_authentication_tracking.conf
#IncludeOptional /etc/modsecurity/optional_rules/modsecurity_crs_10_ignore_static.conf
IncludeOptional /etc/modsecurity/git/crs-setup.conf
IncludeOptional /etc/modsecurity/git/REQUEST-901-INITIALIZATION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9001-DRUPAL-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9003-NEXTCLOUD-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9004-DOKUWIKI-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-903.9005-CPANEL-EXCLUSION-RULES.conf
IncludeOptional /etc/modsecurity/git/REQUEST-905-COMMON-EXCEPTIONS.conf
IncludeOptional /etc/modsecurity/git/REQUEST-910-IP-REPUTATION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-911-METHOD-ENFORCEMENT.conf
IncludeOptional /etc/modsecurity/git/REQUEST-912-DOS-PROTECTION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-913-SCANNER-DETECTION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-914-FILE-DETECTION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-920-PROTOCOL-ENFORCEMENT.conf
IncludeOptional /etc/modsecurity/git/REQUEST-921-PROTOCOL-ATTACK.conf
IncludeOptional /etc/modsecurity/git/REQUEST-930-APPLICATION-ATTACK-LFI.conf
IncludeOptional /etc/modsecurity/git/REQUEST-931-APPLICATION-ATTACK-RFI.conf
IncludeOptional /etc/modsecurity/git/REQUEST-932-APPLICATION-ATTACK-RCE.conf
IncludeOptional /etc/modsecurity/git/REQUEST-933-APPLICATION-ATTACK-PHP.conf
IncludeOptional /etc/modsecurity/git/REQUEST-941-APPLICATION-ATTACK-XSS.conf
IncludeOptional /etc/modsecurity/git/REQUEST-942-APPLICATION-ATTACK-SQLI.conf
IncludeOptional /etc/modsecurity/git/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf
IncludeOptional /etc/modsecurity/git/REQUEST-944-APPLICATION-ATTACK-JAVA.conf
IncludeOptional /etc/modsecurity/git/REQUEST-949-BLOCKING-EVALUATION.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-950-DATA-LEAKAGES.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-951-DATA-LEAKAGES-SQL.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-952-DATA-LEAKAGES-JAVA.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-953-DATA-LEAKAGES-PHP.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-954-DATA-LEAKAGES-IIS.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-959-BLOCKING-EVALUATION.conf
IncludeOptional /etc/modsecurity/git/RESPONSE-980-CORRELATION.conf
SecAuditEngine On
# SecAuditEngine RelevantOnly
# SecAuditLogRelevantStatus ^1-5
# SecAuditLogParts ABCIFHZ
SecAuditLogType Serial
SecAuditLog /var/log/apache2/modsec_audit.log
</VirtualHost>
andrea
- Published in Networking, Sistemistica, Tips & Tricks
Debian Bonding LACP con Switch HP 1820-24G
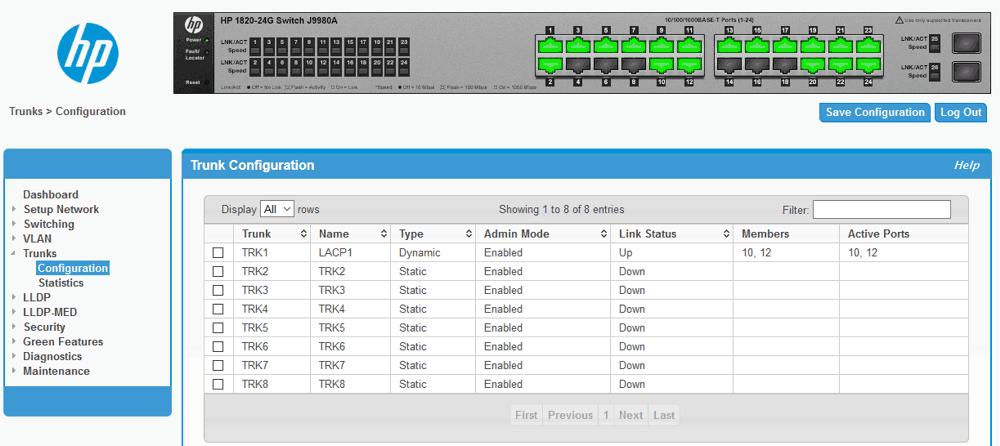
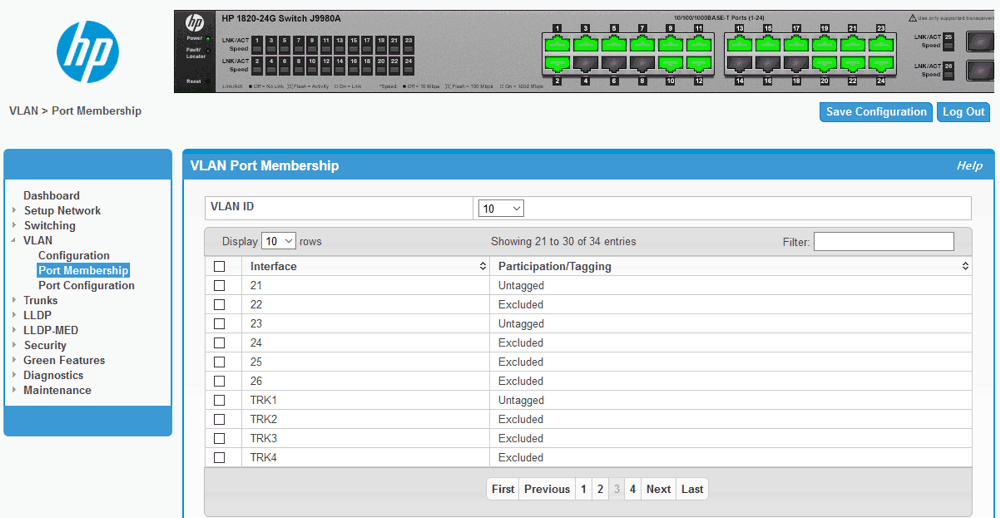
Una volta configurato lo switch HP 1820-24G Switch J9980A per avere il port trunking tra le porte selezionate ed eventualmente aver assegnato il trunk alla VLAN si passa alla configurazione del sistema.
Attenzione che HP chiama Trunk dinamico la modalità LACP.
Ho trovato in alcuni howto questa specifica.
Male non dovrebbe fare.
echo "mii" >> /etc/modules
Si passa alla configurazione dell file /etc/network/interfaces in questo modo.
auto lo
iface lo inet loopback
iface enp2s0f0 inet manual
post-up ifconfig enp2s0f0 txqueuelen 5000 && ifconfig enp2s0f0 mtu 9000
iface enp2s0f1 inet manual
post-up ifconfig enp2s0f1 txqueuelen 5000 && ifconfig enp2s0f1 mtu 9000
auto bond0
iface bond0 inet manual
bond-slaves enp2s0f0 enp2s0f1
bond-mode 802.3ad
bond-miimon 100
bond-downdelay 200
bond-updelay 200
bond-lacp-rate 1
bond-xmit-hash-policy layer2+3
post-up ifconfig bond0 mtu 9000 && ifconfig bond0 txqueuelen 5000
auto vmbr0
iface vmbr0 inet static
address 172.16.5.10
netmask 255.255.255.0
bridge_ports bond0
bridge_stp off
bridge_fd 0
post-up ifconfig vmbr0 mtu 9000 && ifconfig vmbr0 txqueuelen 5000
A questo punto dopo il riavvio il Bond/Trunk risulterà attivo.
# dmesg
igb 0000:02:00.0 enp2s0f0: igb: enp2s0f0 NIC Link is Up 1000 Mbps Full Duplex, Flow Control: None bond0: link status up for interface enp2s0f0, enabling it in 0 ms bond0: link status definitely up for interface enp2s0f0, 1000 Mbps full duplex bond0: Warning: No 802.3ad response from the link partner for any adapters in the bond bond0: first active interface up! vmbr0: port 1(bond0) entered blocking state vmbr0: port 1(bond0) entered forwarding state IPv6: ADDRCONF(NETDEV_CHANGE): vmbr0: link becomes ready igb 0000:02:00.1 enp2s0f1: igb: enp2s0f1 NIC Link is Up 1000 Mbps Full Duplex, Flow Control: None bond0: link status up for interface enp2s0f1, enabling it in 200 ms bond0: link status definitely up for interface enp2s0f1, 1000 Mbps full duplex
# cat /proc/net/bonding/bond0
Ethernet Channel Bonding Driver: v3.7.1 (April 27, 2011)
Bonding Mode: IEEE 802.3ad Dynamic link aggregation
Transmit Hash Policy: layer2+3 (2)
MII Status: up
MII Polling Interval (ms): 100
Up Delay (ms): 200
Down Delay (ms): 200
802.3ad info
LACP rate: fast
Min links: 0
Aggregator selection policy (ad_select): stable
System priority: 65535
System MAC address: 90:e2:ba:74:28:f8
Active Aggregator Info:
Aggregator ID: 1
Number of ports: 2
Actor Key: 9
Partner Key: 54
Partner Mac Address: 70:10:6f:71:3a:80
Slave Interface: enp2s0f0
MII Status: up
Speed: 1000 Mbps
Duplex: full
Link Failure Count: 0
Permanent HW addr: 90:e2:ba:74:28:f8
Slave queue ID: 0
Aggregator ID: 1
Actor Churn State: none
Partner Churn State: none
Actor Churned Count: 0
Partner Churned Count: 0
details actor lacp pdu:
system priority: 65535
system mac address: 90:e2:ba:74:28:f8
port key: 9
port priority: 255
port number: 1
port state: 63
details partner lacp pdu:
system priority: 32768
system mac address: 70:10:6f:71:3a:80
oper key: 54
port priority: 128
port number: 12
port state: 61
Slave Interface: enp2s0f1
MII Status: up
Speed: 1000 Mbps
Duplex: full
Link Failure Count: 0
Permanent HW addr: 90:e2:ba:74:28:f9
Slave queue ID: 0
Aggregator ID: 1
Actor Churn State: none
Partner Churn State: none
Actor Churned Count: 0
Partner Churned Count: 0
details actor lacp pdu:
system priority: 65535
system mac address: 90:e2:ba:74:28:f8
port key: 9
port priority: 255
port number: 2
port state: 63
details partner lacp pdu:
system priority: 32768
system mac address: 70:10:6f:71:3a:80
oper key: 54
port priority: 128
port number: 10
port state: 61
andrea
- Published in Networking, Sistemistica, Tips & Tricks
Bond tra interfacce di rete in Proxmox
Avendo più interfacce di rete disponibili ed utilizzando switch dotati di link aggregation è possibile unire le interfacce in un bond sul quale appoggiare il bridge.
Questo deve essere configurato manualmente in quanto l’interfaccia web di proxmox non prevede questo utilizzo.
/etc/network/interfaces
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet manual
bond-master bond0
mtu 9000
auto eth1
iface eth1 inet manual
bond-master bond0
mtu 9000
auto bond0
iface bond0 inet manual
mtu 9000
bond-mode 802.3ad
bond-miimon 100
bond-slaves none
bond-lacp-rate 4
auto vmbr0
iface vmbr0 inet static
mtu 9000
address 192.168.1.1
netmask 255.255.255.0
network 192.168.1.0
bridge_ports bond0
bridge_stp off
bridge_fd 0
post-up route add -net 10.1.1.0 netmask 255.255.255.0 gw 192.168.2.254
pre-down route del -net 10.1.1.0 netmask 255.255.255.0 gw 192.168.2.254
Il traffico di rete si distribuirà in modo automatico (e non bilanciato) sulle due interfacce aumentando sensibilmente la banda di rete utilizzata.
# ifconfig eth0
eth0 Link encap:Ethernet HWaddr 00:26:55:ec:ef:b6
UP BROADCAST RUNNING SLAVE MULTICAST MTU:1500 Metric:1
RX packets:82172110 errors:0 dropped:0 overruns:0 frame:0
TX packets:366333813 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:32549246640 (30.3 GiB) TX bytes:1142227109649 (1.0 TiB)
Interrupt:24 Memory:feb80000-feba0000
# ifconfig eth1
eth1 Link encap:Ethernet HWaddr 00:26:55:ec:ef:b6
UP BROADCAST RUNNING SLAVE MULTICAST MTU:1500 Metric:1
RX packets:543001774 errors:0 dropped:0 overruns:0 frame:0
TX packets:366337469 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:237725677253 (221.3 GiB) TX bytes:469115298143 (436.8 GiB)
Andrea – Netlite.it
- Published in Sistemistica, Tips & Tricks, Virtualizzazione